Cyberthreats targeting the 2025 holiday season
 |
The findings reveal a clear trend: attackers are moving faster, automating more, and capitalising fully on the seasonal surge, according to the FortiRecon Cyberthreat Landscape Overview for the 2025 Holiday Season from FortiGuard Labs.
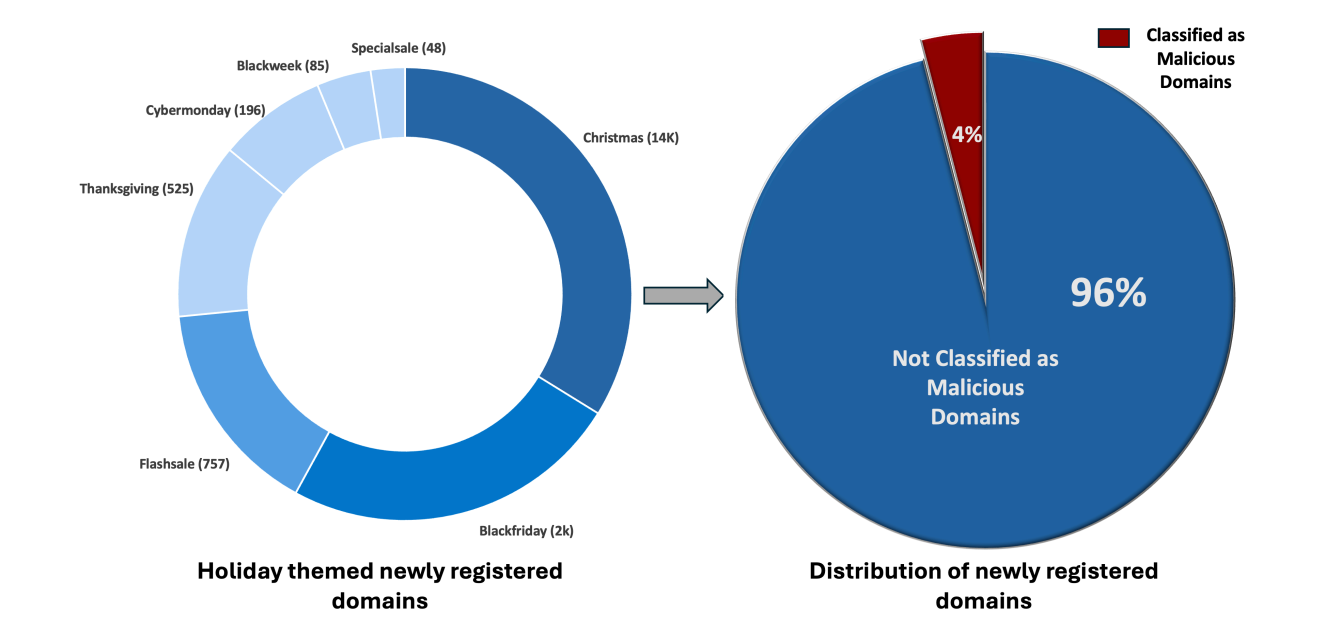
One of the clearest indicators of pre-holiday attacker activity is domain registration. FortiGuard identified more than 18,000 holiday-themed domains registered in the past three months, including terms such as “Christmas”, “Black Friday”, and “Flash Sale”. At least 750 of these were confirmed malicious. This indicates many domains are still considered non-malicious, posing a potential risk.
A parallel surge occurred among domains imitating major retail brands. Attackers registered over 19,000 e-commerce-themed domains, of which 2,900 were malicious. Many mimic household names, often with slight variations that are easy to miss when shoppers are moving quickly.
These domains support phishing, fraudulent storefronts, gift card scams, and payment-harvesting schemes. They also contribute to SEO poisoning campaigns that artificially inflate malicious URLs in search results during peak shopping events.
The report also shows a striking increase in the availability and use of stealer logs. Over the last three months, more than 1.57 million login accounts tied to major e-commerce sites, available through stealer logs, were collected across underground markets.
Stealer logs contain browser-stored passwords, cookies, session tokens, autofill data, and system fingerprints. During the holidays, users log in to multiple accounts across devices, making these logs especially valuable.
Criminal marketplaces now index these logs with search filters, reputation scores, and automated delivery systems. This significantly reduces the skill barrier, enabling rapid credential stuffing, account takeover, and unauthorised purchases.
The report also notes active “holiday sales” on card dumps and CVV datasets. Threat actors use Black Friday-style promotions to push stolen financial data at discounted prices, fuelling an uptick in fraud.
Critical vulnerabilities in e-commerce platforms
Attackers are actively exploiting vulnerabilities across Adobe/Magento, Oracle E-Business Suite, WooCommerce, Bagisto, and other common e-commerce platforms. Three vulnerabilities stand out:
- CVE-2025-54236 (Adobe/Magento)
Public reporting suggests this vulnerability is being exploited to achieve session takeover and remote code execution through improper input validation. More than 250 Magento stores have shown signs of compromise.
- CVE-2025-61882 (Oracle EBS)
Used by ransomware groups to execute unauthenticated remote code execution, steal ERP data, and disrupt order and inventory systems.
- CVE-2025-47569 (WordPress WooCommerce Ultimate Gift Card plugin)
Poses a significant security risk to WooCommerce-based online stores, as successful exploitation could allow attackers to manipulate or exfiltrate sensitive database information. Threat actors in the darknet are selling access to database data by exploiting this vulnerability.
Across platforms, vulnerabilities in plugins, templates, and API authentication are enabling payment skimming, XSS exploitation, privilege escalation, and unauthorised file uploads.
Magecart-style JavaScript injection remains one of the most persistent and damaging threats, allowing attackers to skim payment data directly from checkout pages.
In addition, this year’s threat activity is driven by a high level of automation, supported by a mature ecosystem of services that eliminates the need for attackers to build their own tools or infrastructure. AI-powered brute-force frameworks now handle large volumes of login attempts with human-like timing and behaviour, making credential attacks more difficult to detect.
Instant-setup hosting for phishing pages or malware delivery has become a staple offering, providing attackers with ready-made servers that require minimal configuration. New website-cloning services can reproduce full storefronts for use in fraud campaigns, while automated SIP platforms support high-volume vishing attempts with spoofed caller IDs. SMS spam panels extend these capabilities into smishing campaigns, letting attackers target shoppers with fake delivery notices or discount offers.
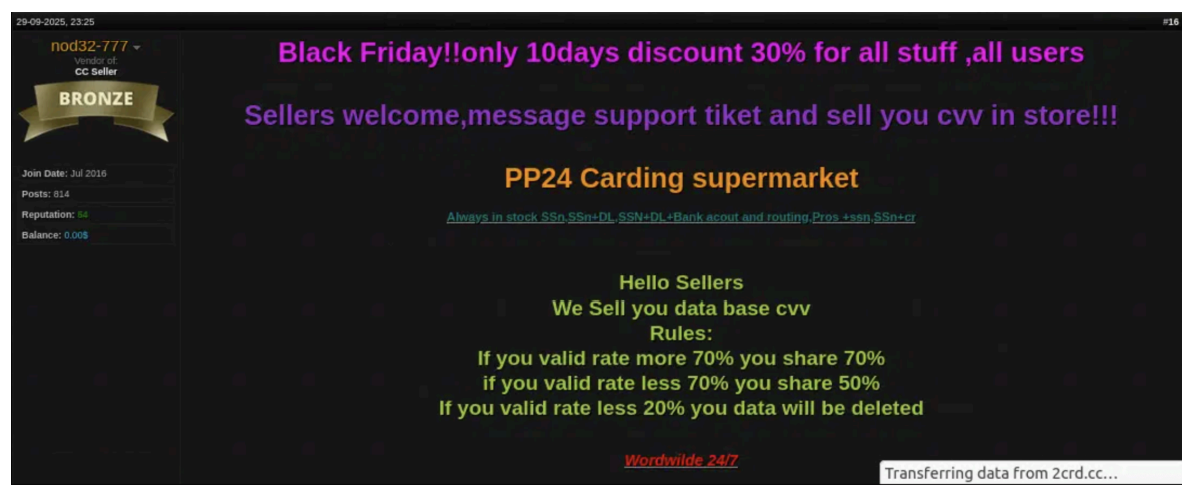 |
Furthermore, underground markets are showing a clear rise in listings tied to e-commerce compromise, and the scale reflects how organised these operations have become. Threat actors are selling full customer databases pulled from breached online stores, along with millions of leaked WooCommerce records containing shopper and merchant details.
Payment tokens and customer contact information appear frequently, as do browser cookies that allow buyers to bypass passwords and multifactor authentication (MFA) altogether. Some listings even offer administrative or FTP access to high-revenue retail sites, giving attackers direct control over backend systems. Others are recruiting accomplices for cash-out operations, enabling rapid laundering or monetisation of stolen balances and fraudulent purchases.
Overall, the traditional holiday spike in cyber activity now intersects with large stealer-log ecosystems, commodity AI tooling, and widespread vulnerabilities in e-commerce infrastructure. For chief information security officers, fraud teams, and e-commerce leaders, this is not a temporary challenge confined to the holiday window. It reflects broader trends in attacker tooling and monetisation that will persist into 2026. The following best practices outline what organisations and consumers can do to stay ahead of the most common threats during the 2025 shopping season.
Best practices for organisations
- Keep all e-commerce platforms, plugins, themes, and third-party integrations fully updated, and remove anything not being used
- Enforce HTTPS everywhere and secure session cookies, administrative pages, and checkout flows
- Require MFA on administrative and high-risk accounts and enforce strong password policies
- Use bot management, rate limiting, and anomaly detection tools to reduce credential abuse
- Monitor for deceptive or lookalike domains impersonating your brand and act quickly on takedowns
- Scan for unauthorised script changes and deploy controls to detect payment page tampering or skimmers
- Centralise logging to monitor for suspicious administrative actions, session hijacking, or unusual database access
- Ensure that your fraud, security, and customer support teams follow a shared cyber-event escalation path throughout the holiday period
Best practices for end-users
- Verify website URLs carefully before entering login or payment information
- Use credit cards or trusted payment processors that offer fraud protection
- Enable MFA on shopping, email, and banking accounts
- Avoid public Wi-Fi or use a VPN when making purchases or managing financial accounts
- Be cautious with unsolicited messages and unrealistic promotions, particularly those tied to deliveries or discounts
- Review your bank and card statements regularly to quickly detect unauthorised charges
 | Fortinet advances quantum-safe security Fortinet has announced innovations within its unified operating system, FortiOS, that protect against quantum-computing threats to current encryption standards. |
 | Rising data security budgets fail to curb insider breaches Organisations worldwide are boosting investment in safeguarding sensitive information, but insider threats remain a costly weak spot. |
 | AI adoption in cybersecurity surges across Vietnam Fortinet has announced the findings of a 2025 IDC survey highlighting how organisations across Vietnam are adopting AI as the front line of their cyber defence strategy. |
What the stars mean:
★ Poor ★ ★ Promising ★★★ Good ★★★★ Very good ★★★★★ Exceptional
 Tag:
Tag:
Related Contents
Latest News
More News
- Agentic AI set to reshape Vietnam’s enterprise landscape (February 10, 2026 | 12:06)
- Agro-forestry and fisheries exports jump nearly 30 per cent in January (February 09, 2026 | 17:45)
- Canada trade minister to visit Vietnam and Singapore (February 09, 2026 | 17:37)
- New tax incentives to benefit startups and SMEs (February 09, 2026 | 17:27)
- Vietnam forest protection initiative launched (February 07, 2026 | 09:00)
- China buys $1.5bn of Vietnam farm produce in early 2026 (February 06, 2026 | 20:00)
- Vietnam-South Africa strategic partnership boosts business links (February 06, 2026 | 13:28)
- Mondelez Kinh Do renews the spirit of togetherness (February 06, 2026 | 09:35)
- Seafood exports rise in January (February 05, 2026 | 17:31)
- Accelerating digitalisation of air traffic services in Vietnam (February 05, 2026 | 17:30)






















 Mobile Version
Mobile Version