FortiGuard Labs warn of destructive wiper malware increase
 |
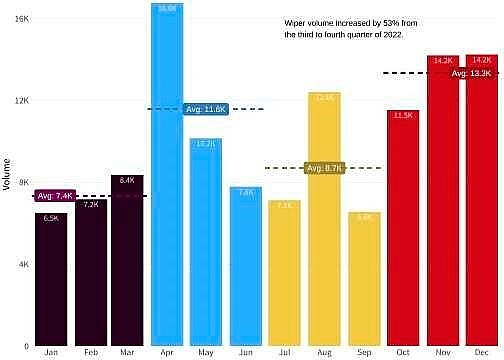
| FortiGuard Labs warn that the wiper malware has increased by over 50 per cent (Source: Fortinet) |
Fortinet, a global cybersecurity leader driving the convergence of networking and security, announced the latest biannual Global Threat Landscape Report from FortiGuard Labs on February 28.
The report indicates that the threat landscape and organisations’ attack surface is constantly transforming, and cybercriminals’ ability to design and adapt their techniques to suit this evolving environment continues to pose significant risks to businesses of all sizes, regardless of industry or geography.
Notably, the report highlights that destructive APT-like wiper malware spread widely in 2022. Analysing malware data reveals the consistent use of destructive attack techniques against targets. It also shows that, with the lack of borders on the internet, cyber groups can easily scale these types of attacks which have been largely enabled by the Cybercrime-as-a-Service model.
In early 2022, FortiGuard Labs reported the presence of several new wipers in parallel with the Russia-Ukraine war. Later in the year, wiper malware expanded into other countries, fuelling a 53 per cent increase in wiper activity from Q3 to Q4 alone.
While some of this activity was enabled by wiper malware that may have been initially developed and deployed by nation-state actors surrounding the war, it is being picked up by cybercriminal groups and is spreading beyond just Europe.
Unfortunately, the trajectory of destructive wiper malware does not appear to be slowing any time soon based on the activity volume seen in Q4, which means any organisation remains a potential target, not just those based in Ukraine or surrounding countries.
 |
| Wiper malware volume |
Another highlight of the report is that financially motivated cybercrime and ransomware threat holding has also reached peak levels. FortiGuard Labs Incident Response engagements found that financially motivated cybercrime resulted in the highest volume of incidents (73.9 per cent), with a distant second attributed to espionage (13 per cent).
Throughout last year, 82 per cent of financially motivated cybercrime involved the employment of ransomware or malicious scripts, showing that the global ransomware threat remains in full force with no evidence of slowing down thanks to the growing popularity of Ransomware-as-a-Service (RaaS) on the dark web.
In fact, the ransomware volume increased by 16 per cent from the first half of 2022. Out of a total of 99 observed ransomware families, the top five accounted for roughly 37 per cent of all ransomware activity during H2/2022.
GandCrab, a RaaS malware that emerged in 2018, was at the top of the list. Although the criminals behind GandCrab announced that they were retiring after making over $2 billion in profits, many iterations of GandCrab were produced during its active time.
Country manager of Fortinet Vietnam Nguyen Gia Duc said, “For cyber criminals, maintaining access and evading detection is no small feat as cyber defences continue to advance to protect organisations. To counter this, adversaries are augmenting more reconnaissance techniques and deploying more sophisticated attack alternatives to enable their destructive attempts with APT-like threat methods such as wiper malware or other advanced payloads.”
“To protect against these persistent cybercrime tactics, focus must be placed on enabling machine learning-driven, coordinated, and actionable threat intelligence in real time across all security devices to detect suspicious actions and initiate coordinated mitigation across the extended attack surface,” Duc added.
Since the second half of 2022, new intelligence allows chief information security officers to prioritise risk mitigation efforts and minimise the active attack surface with the expansion of the Red Zone approach.
The most prevalent malware is more than a year old and has gone through a large amount of speciation, highlighting the efficacy and economics of reusing and recycling code. Furthermore, Log4j continues to impact organisations in all regions and industries, most notably across technology, government, and education.
Predicting for 2023, Nguyen Minh Hai, systems engineer manager at Fortinet Vietnam said, “Wipers on their own are destructive in nature. Combining them with other attack vectors is one of the biggest emerging threats we are facing, as it allows malware to replicate and spread quickly.”
“In addition, the time to detection and the speed at which security teams can remediate is paramount. The commoditisation of wipers gives them the potential to impact networks on an exponential scale,” Hai said.
 | Fortinet aims to narrow cybersecurity skill gap Fortinet has pledged to train one million professionals by 2026 to contribute to narrowing the current cybersecurity skills shortfall. |
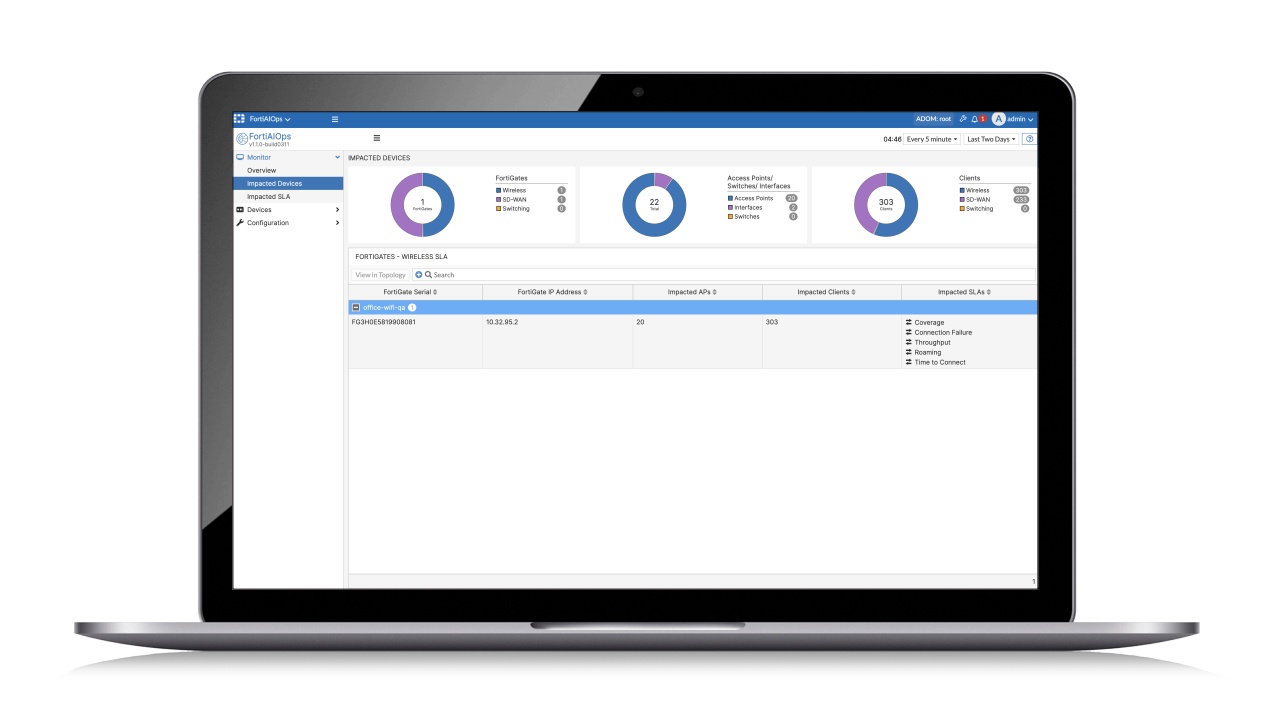 | Fortinet introduces enhanced AIOps capabilities Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, has recently announced enhanced artificial intelligence operations (AIOps) capabilities across its entire networking portfolio, including the industry’s first AI-based network operations management for 5G/LTE gateways. |
 | Fortinet surpasses one million issued network security expert certificates Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, has recently announced it has issued more than one million network security expert (NSE) certifications to date, further advancing its commitment to close the cybersecurity skills gap. |
 | Fortinet launches State of Operational Technology and Cybersecurity Report At today's conference to announce Fortinet’s global 2022 State of Operational Technology (OT) and Cybersecurity Report, experts exchange crucial information on the risk of OT security. |
What the stars mean:
★ Poor ★ ★ Promising ★★★ Good ★★★★ Very good ★★★★★ Exceptional
Related Contents
Latest News
More News
- Agro-forestry and fisheries exports jump nearly 30 per cent in January (February 09, 2026 | 17:45)
- Canada trade minister to visit Vietnam and Singapore (February 09, 2026 | 17:37)
- New tax incentives to benefit startups and SMEs (February 09, 2026 | 17:27)
- Vietnam forest protection initiative launched (February 07, 2026 | 09:00)
- China buys $1.5bn of Vietnam farm produce in early 2026 (February 06, 2026 | 20:00)
- Vietnam-South Africa strategic partnership boosts business links (February 06, 2026 | 13:28)
- Mondelez Kinh Do renews the spirit of togetherness (February 06, 2026 | 09:35)
- Seafood exports rise in January (February 05, 2026 | 17:31)
- Accelerating digitalisation of air traffic services in Vietnam (February 05, 2026 | 17:30)
- Ekko raises $4.2 million to improve employee retention and financial wellbeing (February 05, 2026 | 17:28)

 Tag:
Tag:




















 Mobile Version
Mobile Version