Dark web activity shows cybercriminals targeting Olympics
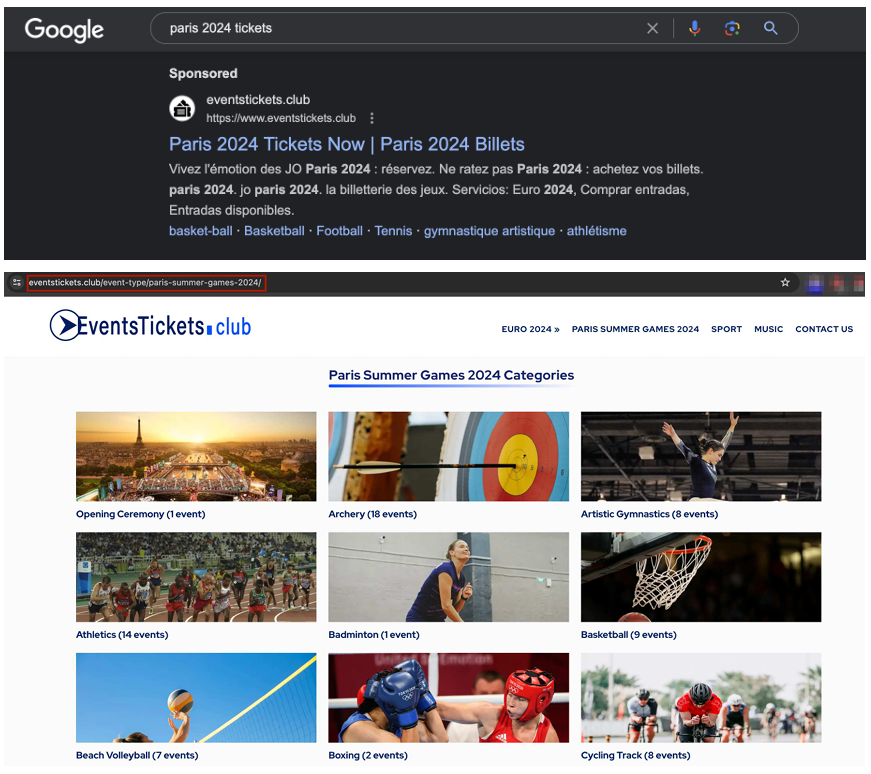 |
| Malicious websites linked to Olympics-related events |
FortiGuard Labs has observed a significant increase in resources being gathered for the Paris Olympic Games, especially those targeting French-speaking users, French government agencies and businesses, and French infrastructure providers. Beginning the second half of 2023, there was a surge in darknet activity targeting France.
This 80 per cent to 90 per cent increase has remained consistent across the second half of 2023 and the first half of 2024. The prevalence and sophistication of these threats are a testament to cybercriminals’ planning and execution, with the dark web serving as a hub for their activities.
Documented activities include the growing availability of advanced tools and services designed to accelerate data breaches and gather personally identifiable information (PII), the sale of stolen credentials and compromised VPN connections to enable unauthorised access to private networks, and advertisements for phishing kits and exploit tools customised for the Paris Olympics. They also include the sale of French databases that contain sensitive personal information, as well as combo lists (a collection of compromised usernames and passwords used for automated brute-force attacks) of French citizens.
Given that Russia and Belarus are not invited to this year’s games, there has also been a spike in hacktivist activity by pro-Russian groups, like LulzSec, noname057(16), Cyber Army Russia Reborn, Cyber Dragon, and Dragonforce, that specifically say they’re targeting the Olympic Games. Groups from other countries and regions are also prevalent, including Anonymous Sudan (Sudan), Gamesia Team (Indonesia), Turk Hack Team (Turkey), and Team Anon Force (India).
While phishing is perhaps the easiest form of attack, many low-sophistication cybercriminals don’t know how to create or distribute phishing emails. Phishing kits provide novice attackers with a simple user interface that helps them compose a convincing email, add a malicious payload, create a phishing domain, and procure a list of potential victims. The addition of text-generating AI services has also eliminated the spelling, grammatical, and graphical errors that allow recipients to detect an email as malicious.
The FortiGuard Labs team has also documented a significant number of typosquatting domains registered around the Olympics, including variations on the name (oympics[.]com, olmpics[.]com, olimpics[.]com, and others). These are combined with cloned versions of the official ticket website that take users to a payment method where they don’t get a ticket, and their money is gone.
In collaboration with Olympic partners, the French Gendarmerie Nationale has identified 338 fraudulent websites claiming to sell Olympic tickets. According to their data, 51 sites have been shut down, and 140 have received formal notices from law enforcement.
Similarly, several Olympic Games–themed lottery scams have been identified, with many impersonating major brands such as Coca-Cola, Microsoft, Google, the Turkish National Lottery, and the World Bank. The primary targets for these lottery scams are users in the United States, Japan, Germany, France, Australia, the United Kingdom, and Slovakia.
There has also been an increase in coding services for creating phishing websites and associated live panels, bulk SMS services to enable mass communication, and phone number spoofing services. These offerings can facilitate phishing attacks, spread misinformation, and disrupt communications by impersonating trusted sources, potentially causing significant operational and security challenges during the event.
In addition, information stealer malware is designed to stealthily infiltrate a victim’s computer or device and harvest sensitive information, such as login credentials, credit card details, and other personal data. Threat actors are deploying various types of stealer malware to infect user systems and obtain unauthorised access. Threat actors and initial access brokers can further leverage this information to execute ransomware attacks, causing substantial harm and financial loss to individuals and organisations.
FortiGuard Labs' data indicates that Raccoon is currently the most active info-stealer in France, accounting for 59 per cent of all detections. Raccoon is an effective and inexpensive malware-as-a-service (MaaS) sold on dark web forums. It steals browser autofill passwords, history, cookies, credit cards, usernames, passwords, cryptocurrency wallets, and other sensitive data. It is followed by Lumma (another subscription-based MaaS) at 21 per cent, and Vidar at 9 per cent.
In addition to celebrating athleticism and sportsmanship, the Paris Olympics 2024 are a high-stakes cyberthreat target, drawing attention from cybercriminals, hacktivists, and state-sponsored actors. Cybercriminals are leveraging phishing scams and fraudulent schemes to exploit unsuspecting participants and spectators.
Fake ticketing platforms, fraudulent merchandise, and identity theft tactics threaten financial loss and undermine public trust in event-related transactions. Further, due to France’s political stances and international influence, the Paris Olympics 2024 is also a prime target for politically motivated groups.
FortiGuard Labs anticipates that hacktivist groups will focus on entities associated with the Paris Olympics to disrupt the event, targeting infrastructure, media channels, and affiliated organisations to disrupt event proceedings, undermine credibility, and amplify their messages on a global stage.
 | Threat actors increasingly targeting operational technology organisations Nearly one-third (31 per cent) of operational technology (OT) organisations reported more than six intrusions in the last year, up from 11 per cent the year before, according to Fortinet's latest findings. |
 | Fortinet and Samsung Heavy Industries sign MoU on maritime cybersecurity On March 27, Fortinet, the global cybersecurity leader driving the convergence of networking and security, and Samsung Heavy Industries, a global leader in maritime shipbuilding, announced the signing of an MoU for cooperation in the maritime cybersecurity of ships. |
 | Fortinet reaffirms its commitment to secure product development and responsible disclosure processes As one of the first cybersecurity vendors to sign CISA’s Secure by Design pledge, Fortinet® (NASDAQ: FTNT) is dedicated to a culture of responsible radical transparency that puts the safety of customers first. |
What the stars mean:
★ Poor ★ ★ Promising ★★★ Good ★★★★ Very good ★★★★★ Exceptional
 Tag:
Tag:
Related Contents
Latest News
More News
- Agro-forestry and fisheries exports jump nearly 30 per cent in January (February 09, 2026 | 17:45)
- Canada trade minister to visit Vietnam and Singapore (February 09, 2026 | 17:37)
- New tax incentives to benefit startups and SMEs (February 09, 2026 | 17:27)
- Vietnam forest protection initiative launched (February 07, 2026 | 09:00)
- China buys $1.5bn of Vietnam farm produce in early 2026 (February 06, 2026 | 20:00)
- Vietnam-South Africa strategic partnership boosts business links (February 06, 2026 | 13:28)
- Mondelez Kinh Do renews the spirit of togetherness (February 06, 2026 | 09:35)
- Seafood exports rise in January (February 05, 2026 | 17:31)
- Accelerating digitalisation of air traffic services in Vietnam (February 05, 2026 | 17:30)
- Ekko raises $4.2 million to improve employee retention and financial wellbeing (February 05, 2026 | 17:28)






















 Mobile Version
Mobile Version