VNDirect cyberattack causes big splash on stock market
 |
| VNDirect cyberattack causes big splash on stock market, illustration photo/ Source: freepik.com |
VNDirect Cyber System has been under attack since March 24. It has been three days since the temporary shutdown, and VNDirect's online securities trading system has yet to resume operations.
VNDirect said it has been making efforts to restore the system, and all customer data is safe. The securities firm is in the process of reconnecting the system, but the process is taking longer than expected.
“VNDirect was attacked by a group of professional hackers who encrypted our company data. We have now completed decrypting the blocked data and starting to restore the system," Nguyen Vu Long, CEO of VNDirect, said.
Based on information shared by VNDirect, Vu Ngoc Son, technical director of the Vietnam National Cybersecurity Technology Corporation (NCS), said, the company once information has been encrypted, there is almost no way to deal with it in the short term. Therefore, organisations often have to pay to receive recovery passwords.
Following the cyberattack, Hanoi Stock Exchange (HNX) announced it was temporarily disconnecting remote trading and online trading of derivative securities transactions, debt instrument transactions, and individual corporate bond transactions of VNDirect Securities until the problem is resolved.
VNDirect is not the first financial company to be attacked in the industry. However, the incident made a big splash as it affected a large number of users.
"After restoring the data, it will take time to recover the system to avoid information leaks and ensure safety from other risks," he commented.
Sophos, a global leader in innovating and delivering cybersecurity, noted in its annual 2024 Sophos Threat Report that the greatest cybersecurity challenge facing all businesses is data protection. More than 90 per cent of attacks reported by its customers involve data or credential theft in one way or another, whether the method is a ransomware attack, data extortion, unauthorised remote access, or simply data theft.
In 2023, nearly 50 per cent of malware detections for small- and medium-sized businesses (SMBs) were keyloggers, spyware, and stealers, malware that attackers use to steal data and credentials. Attackers subsequently use this stolen information to gain unauthorised remote access, extort victims, deploy ransomware, and more.
Business email compromise (BEC), in which email accounts are taken over by a cybercriminal for the purpose of fraud or other malicious purposes, is a substantial problem in the SMB set. It is estimated that in 2023, business email compromises were identified by the Sophos Incident Response team more often than any other type of incident, save ransomware.
Stolen credentials, including browser cookies, can be used for BEC, access to third-party services such as cloud-based finance systems, and access to internal resources that can be exploited for fraud or other monetary gain. They can also be sold by “access brokers” to anyone who cares to exploit them. Sophos has tracked offers on underground forums claiming to provide access to a number of SMBs’ networks.
“The value of data as currency has increased exponentially among cybercriminals, and this is particularly true for SMBs, which tend to use one service or software application per function for their entire operations. For example, let’s say attackers deploy an infostealer on their target’s network to steal credentials and then get hold of the password for the company’s accounting software. Attackers could then gain access to the targeted company’s financials and have the ability to funnel funds into their own accounts,” said Christopher Budd, director of Sophos X-Ops Research.
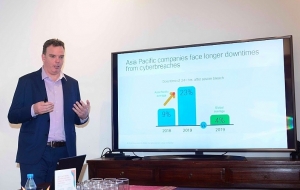 | Vietnamese companies facing longer downtimes from cyber breaches Organisations in Vietnam are facing longer downtimes from cybersecurity breaches, compared to the regional and global averages, according to Cisco’s 2019 Asia-Pacific CISO Benchmark Study. |
 | Cyberattacks more prevalent as online work comes into fashion Local companies are on edge due to their great exposure to cyberattacks through overseas work-from-home services that are their only choice to maintain the workload for employees amidst the COVID-19 lockdown. |
 | 200 business hit in cyberattack on computer tool A computing network management tool by Kaseya was under cyberattack attack on Friday, prompting the US IT company to urge businesses to shut down servers to avoid ransomware. |
What the stars mean:
★ Poor ★ ★ Promising ★★★ Good ★★★★ Very good ★★★★★ Exceptional
Related Contents
Latest News
More News
- Raised ties reaffirm strategic trust (February 20, 2026 | 14:06)
- Sustained growth can translate into income gains (February 19, 2026 | 18:55)
- The vision to maintain a stable monetary policy (February 19, 2026 | 08:50)
- Banking sector faces data governance hurdles in AI transition (February 19, 2026 | 08:00)
- AI leading to shift in banking roles (February 18, 2026 | 19:54)
- Digital banking enters season of transformation (February 16, 2026 | 09:00)
- IFC to grant $150 million loan package for VPBank (February 13, 2026 | 09:00)
- Nam A Bank forms position as strategic member at VIFC through three key partnerships (February 12, 2026 | 16:39)
- Banks bolster risk buffers to safeguard asset quality amid credit expansion (February 12, 2026 | 11:00)
- VNPAY and NAPAS deepen cooperation on digital payments (February 11, 2026 | 18:21)

 Tag:
Tag:



















 Mobile Version
Mobile Version